Due to the high degree of interconnectivity between devices and IoT Systems, physical components of the devices have become essential targets in Cybersecurity. Hardware penetration testing tools are handy for assessing risks in gadgets such as routers, USB, RFID, and IoT.
In this blog, we have outlined the 7 best tools for hardware pentesting, their functionalities, and how Long Island businesses can integrate them into their security plans.
What is Hardware Penetration Testing?
Hardware penetration testing is the process of testing and evaluating the security of physical hardware devices and systems to identify vulnerabilities, weaknesses, or potential points of exploitation.
The hardware layers include IoT devices, network routers, USB ports, and RFID tags. Such tests are meant to identify potential vulnerabilities in design, firmware, or configurations that would leave the hardware open to hacking or data interception.
For businesses providing cybersecurity services near Long Island, these tools guarantee that the company meets and complies with PI DSS and HIPAA standards while protecting critical hardware from dangers.
7 Tools Commonly Used in Hardware Penetration Testing
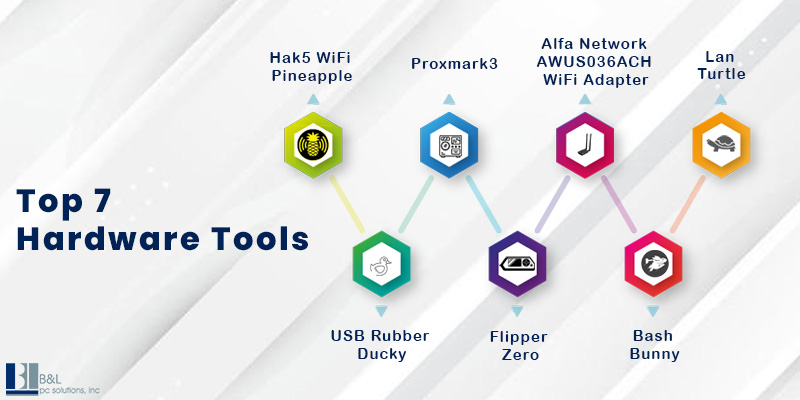
1. Hak5 WiFi Pineapple
The Hak5 WiFi Pineapple program is a valuable penetration testing device on wireless networks. It enables the creation of rogue access points that can control-test real-life conditions, such as man-in-the-middle attacks and packet sniffing. Consequently, cybersecurity professionals often examine weak WiFi configurations in business telemetry.
| Feature | Details |
| Purpose | Wireless network penetration testing |
| Key Features | Rogue AP creation, packet sniffing, MITM attacks |
| Use Case | Identifying weak WiFi security |
| Pricing | ~$120 |
2. USB Rubber Ducky
USB Rubber Ducky is a USB device that looks like a flash drive but injects keystrokes into the PC target. It injects malware disguised as a keyboard so testers can analyze USB port vulnerabilities. Insider threat testing environment is the tool most commonly used in this case.
| Feature | Details |
| Purpose | USB port vulnerability testing |
| Key Features | Keyboard emulation, automated scripts |
| Use Case | Identifying USB-based attack risks |
| Pricing | ~$50 |
3. Proxmark3
Proxmark3 is an RFID and NFC testing tool. It can read and write to RFID tags and copy or replicate them, making testing an access control system extremely valuable. Since it supports multiple RFID standards, it suits our office and industrial security assessments.
| Feature | Details |
| Purpose | RFID and NFC testing |
| Key Features | RFID cloning, emulation, and writing |
| Use Case | Evaluating access control systems |
| Pricing | ~$300 |
4. Flipper Zero
Flipper Zero is now a combined end-to-end hardware testing and vulnerability testing tool that supports NFC, RFID, Bluetooth, and infrared. This tool is handy for IoT exploitation, so its relevance for evaluating smart devices, IIoT, and SMASH systems is paramount.
| Feature | Details |
| Purpose | IoT device security testing |
| Key Features | Multi-protocol support (NFC, RFID, IR, Bluetooth) |
| Use Case | Testing smart home and industrial IoT security |
| Pricing | ~$170 |
5. Lan Turtle
Lan Turtle is a small USB Ethernet adapter that opens up possibilities for internal network reconnaissance. It facilitates modern applications with MITM attack simulation, SSH access, and bulk packet sniffing. It benefits businesses that want to secure internal networks and monitor their state.
| Feature | Details |
| Purpose | Internal network penetration testing |
| Key Features | SSH access, packet sniffing, MITM simulation |
| Use Case | Testing network segmentation |
| Pricing | ~$60 |
6. Bash Bunny
Bash Bunny is an advanced USB attack emulation device. It works as multiple devices, such as mass storage and an Ethernet adapter, and is, therefore, well suited for evaluating insider threats. Its flexibility is derived from its ability to perform various payloads efficiently.
| Feature | Details |
| Purpose | Advanced USB attack testing |
| Key Features | Multi-device emulation, automated payloads |
| Use Case | Simulating insider threats |
| Pricing | ~$100 |
7. Alfa Network AWUS036ACH WiFi Adapter
This WiFi adapter is used explicitly for wireless network auditing. It supports monitor mode and packet injection, extending compatibility with operating systems like Kali Linux. Finding unsuitable encryption standards. The tool is fantastic for scanning for weak encryption protocols. Auditing WiFi networks; another practical program application is scanning networks to determine their adequacy.
| Feature | Details |
| Purpose | Wireless network auditing |
| Key Features | Monitor mode, packet injection |
| Use Case | Auditing weak WiFi encryption |
| Pricing | ~$40 |
Features to Expect From Hardware Penetration Testing Tools
When choosing hardware penetration testing tools, it's important to consider:
-
Protocol Support: Prompt compatibility with the hardware protocols of Bluetooth, NFC, RFID, and ZigBee.
-
Portability: Small size is an excellent advantage as it contributes to using tools in the workplace.
-
Ease of Use: New users may require devices with fewer options, whereas advanced users may need many more options.
-
Integration: Some tools are more usable, particularly when they integrate well with possible platforms like Kali Linux.
-
Customizability: The sophisticated features should enable script writing for suited testing conditions.
Advantages of Hardware Penetration Testing
-
Proactive Security: Close any loopholes attackers may exploit, securing the business's data from exposure.
-
Regulatory Compliance: Hardware testing ensures that technologies comply with benchmark regulations like PCI DSS, HIPAA, and CCPA, thus avoiding fines.
-
Enhanced IoT Protection: While IoT devices were not part of the basic testing, they can be protected from attacks.
-
Employee Awareness: More testing provides better knowledge of physical device threats, improving general security.
-
Improved Business Continuity: One can utilize the potential threats to protect operations during an attack.
Hardware Penetration Testing Tools Challenges
1. Complexity
It involves a good understanding of the cabling and protocols of various hardware and working with embedded systems, which might need to be present in only some IT departments.
2. High Costs
Some tools, such as Proxmark3, can be very costly, especially to players in the small business category.
3. Legal Concerns
Touching unauthorized systems implies legal repercussions, hence the need to seek proper permission.
4.Rapid Evolution:
As new devices are developed regularly, creating new testing methods is essential.
Read More : Top 11 Penetration Testing Tools in 2025 You Need To Know
Conclusion
Hardware devices need protection, as well as other resources, in the framework of any security plan. The availability of gadgets such as Hak5 WiFi Pineapple and Proxmark3 helps businesses navigate risks properly.
B&L PC Solutions provides businesses with professional IT services on Long Island, including your equipment and property.
Keep your hardware devices safe with professional cybersecurity services from B&L PC Solutions. Contact us today!
Frequently Asked Questions: Hardware Penetration Testing Tools
Q1: What is hardware penetration testing?
Hardware penetration testing involves security testers trying to penetrate physical devices such as IoT systems, USB ports, and RFID cards.
Q2: What kind of tools are recommended for hardware penetration testing?
The most popular tools are Hak5 WiFi Pineapple, USB Rubber Ducky, Proxmark 3, Flipper Zero, Lan Turtle, Bash Bunny, and Alfa Network AWUS036ACH.
Q3: Is the use of hardware penetration testing tools costly?
Prices stretch from $40 for essential tools to $300 for tools with additional functionalities.
Q4: Do Small businesses require hardware penetration testing?
Small businesses increasingly adopt IoT devices and wireless networks, making hardware testing essential to prevent potential breaches.
Q5: When should hardware penetration testing be done?
Annual testing should be conducted whenever there is an update to the network hardware.
Secure your business' future with secure and dependable cybersecurity services. Contact B&L PC Solutions for professional help right now!
Tags: 7 Tools of Hardware Penetration Testing, Advantages of Hardware Penetration Testing, Hardware Penetration Testing, Hardware Penetration Testing Tools, Hardware Penetration Testing Tools Challenges, What is Hardware Penetration Testing